Wondering Who is Viewing Your Video Surveillance?
Switch to March Networks.
Secure, Standards-Based Solutions for a Fraction of the Cost
For 20 years, March Networks has developed highly secure video solutions trusted by some of the world’s largest businesses. Our holistic approach to cybersecurity involves a 360° view of all aspects of our business, encompassing our products, the people who build them, and the processes that guide us. We’re confident our secure solutions can meet your needs – and for a fraction of the cost. Contact us today to learn about our Verkada trade-in program.
End-to-end encryption
All March Networks products are designed with cybersecurity in mind. Our new X-Series Hybrid Recorders offer the highest level of protection for your data, with complete end-to-end encryption – from camera to recorder to enterprise video management system to client software – with cameras supporting RTP/RTSP over HTTPs.

Trusted by Fortune 500 companies
Our video surveillance solutions are deployed by more than 1,000 banks and credit unions – organizations that demand only the highest cybersecurity standards from their vendors. We participate in extensive security audits with these and our other Fortune 500 customers, examining everything from the security of our products to how we control and protect our software source code.

See who uses March Networks
We work with many of the world’s largest financial institutions, retail brands, cannabis operators and transit authorities, as well as many commercial and government organizations.

A 360° approach to cybersecurity
Designing inherently secure, data-protected solutions is part of March Networks’ DNA, tracing back to our deep roots in information technology and networking.
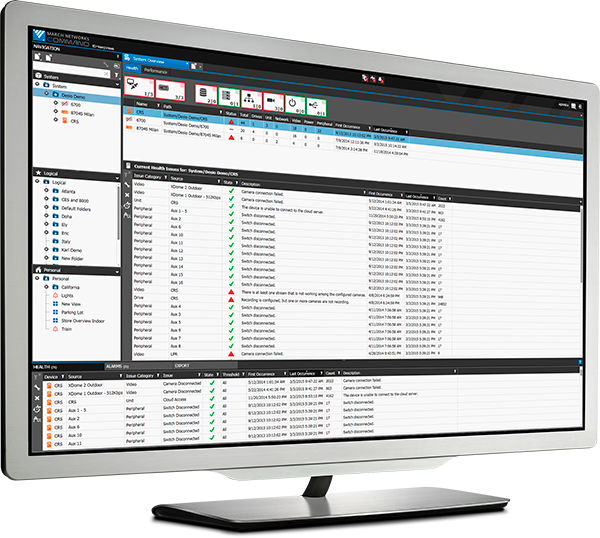
Built-in features to safeguard your data
Because we specialize in enterprise video surveillance, we understand the challenges involved in keeping multiple distributed systems secure. Our Command Enterprise Software is designed with features like customizable user management, supporting LDAP/gSuite integration, so each person in your organization sees only what they need to do their job. Command also offers convenient audit logging features, to track user activity and capture any changes made to the system. It can also alert you to login failures and potential distributed denial-of-service (DDoS) attacks.

Our Linux Operating Systems deliver reliability and security
The Linux-based Operating Systems (OS) in our NVRs are customized to help safeguard against vulnerabilities by removing unnecessary services and applications and locking all non-essential network ports, reducing the likelihood of attack. The customized OS also has a reduced volume of code that helps optimize overall system performance and minimize defects.

Our products pass stringent cybersecurity tests
Our NVRs and IP cameras pass rigorous IT testing, including ethical hacks to assess and resolve potential cyber weaknesses. We also use independent third-party penetration testing to further confirm security integrity.
Rigel Kent Security recently conducted an analysis on March Networks’ recorders. This testing detected no IP-based direct or indirect network communications nor any routing or redirecting of data traffic that could be used to exfiltrate or expose user data.

We offer innovative tools to help strengthen cybersecurity
We designed one of the industry’s first smartphone apps to help with secure video surveillance installations. With our GURU Smartphone App’s Security Audit feature, you can automatically analyze and rate how secure the configuration of installed March Networks recorders is against a list of potential weaknesses. The app then provides guidance where points-of-weaknesses are detected and ways to harden the system.
Contact us to learn more about our Verkada trade-in program
Cybersecurity Brochure
A brochure detailing March Networks' continuing commitment to cybersecurity
Security and Data Protection Overview
March Networks has released a Security and Data Protection Overview that outlines the strategic and proactive approach we are taking to manage cyber risks
March Networks Product Hardening Guide
Recommendations for technicians and systems administrators installing March Networks products to help ensure security
A Guide to GDPR
Read about the European Union's General Data Protection Regulation (GDPR) and how March Networks solutions help customers meet GDPR requirements



