Three Facts about March Networks’ Video Authentication
Filed under: Video Management System, Hybrid NVRs, Technical Support
As product manager for March Networks’ recording platforms, I’m often asked about “watermarking” of surveillance video. I usually point out that watermarking is a process used in photography to show ownership of a photo by superimposing a name, message or symbol overtop of the image. This allows a photographer to share a draft version of the file without fear it will be stolen and shared without their credit. It’s a way for the original creator to prove ownership of the file.
In the video surveillance industry, manufacturers use what could be described as a digital watermarking process to verify the authenticity of video, but I think a better term for this process is “video authentication.”
The Importance of Authentication
Video authentication is important because it underscores the whole purpose of having a video surveillance system; it’s what lets you say with absolute certainty that a particular event happened exactly as it was recorded and depicted in the video.
A decade or so ago, in the age of analog CCTV, the process for handling video evidence was quite manual. A person might physically pull a tape from a recorder and put it into an envelope for safe keeping.
But in the digital age – where having multiple copies of a video file is the norm – it’s essential that video surveillance files be secure, so we can have confidence in their authenticity.
Without some form of proof that a video clip is authentic, video surveillance would be of little use to businesses, law enforcement and the judiciary. For that reason, most manufacturers, including March Networks, accurately timestamp each frame of video and also embed security features that can detect whether anyone has tampered with the file.
Here are three facts that will help you understand more about March Networks’ video authentication process:
- Digital Signature – Before any video is exported from a March Networks recorder, a secure hash algorithm (specifically SHA-256) is applied to the contents of the file, ensuring that any file editing will be detected. Applying a secure hash to a file ensures the integrity of data. In March Networks’ video files, the secure hash provides an anti-tamper function, preventing edited video from being authenticated and rendering it unsuitable for court purposes.
- Authenticating is Easy in Command – Presently, there is no standard method for authenticating video in the surveillance industry. Each manufacturer does it differently. As such, there are no standard players (i.e. Windows Media Player) that are capable of validating the authenticity of video surveillance files. March Networks has a video playback tool, called the Command Player, which can authenticate our video right in the tool. With video loaded in the player, you simply click a button to see if the file is authentic. The below images illustrate this function.
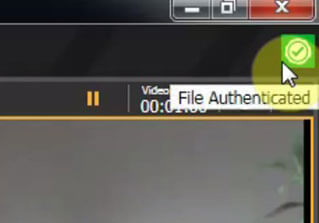 Video File Authenticated
Video File Authenticated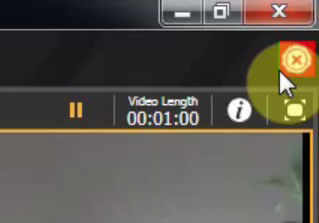 File Inauthentic
File InauthenticThe Command Player enables third-party organizations to review March Networks video without our licensed client software. The Player can be downloaded from our website, but can also be exported and included along with a video clip being sent to a third-party. (For example, if you are a police officer or lawyer working with a business to investigate a crime captured on a March Networks recorder, the person or business supplying you with the video evidence can include the Command Player along with the video file so you will be able to review the clip.)
- Using a Third-Party Player – If you want to playback March Networks video in a third-party application like Windows Media Player, you should export video from your Command Client into an MP4 file format. But – and this is important – if you are viewing March Networks video with a third-party player, you will not see detailed time information, which is key for a criminal investigation, nor will you be able to authenticate the video. For situations like these, March Networks does provide a Command Authentication Tool, which can be used outside of the third-party player to confirm that the exported video file has not been tampered with.
As a global leader in IP video surveillance, March Networks takes pride in keeping its video secure. We go to great lengths to ensure that no one can alter video from our recorders, and if someone tries, our viewing software will detect it.
We also recognize that video evidence must be viewed by many different organizations, and not everyone owns our licensed software. That’s why we’ve created a very secure – yet flexible – authentication system that allows video playback in third-party applications, with the ability to authenticate it using our proprietary tools.
To learn more about using our Command Player, watch this video tutorial.
Comments
Audrey James
Received a disk but unable to authenticate. I am told when I insert the disk it should be a button that I can push. But, I can’t find a button.. Within each files i.e. Rear, Front, Side,, its a check mark within the heading for each. Does that mean its authenticated?
Ken Maughan
Hi Audrey,
Thanks for your question. The pictures in the blog illustrate how to know when the video is authenticated. You can see the check mark at the top right corner.